Recent
Recent
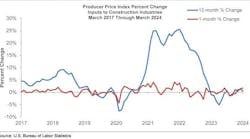
Materials Prices Nudged Upward in March
April 22, 2024
Top Stories
Top Stories
New HVACR Products: April 2024
April 22, 2024
Recommended
Recommended
Download "Refrigerants Revolution 2024"
Dec. 18, 2023
Steril-Aire Celebrates Three Decades of UVC Innovation
April 19, 2024
DOE Releases Roadmap for Connecting Projects to Grid
April 19, 2024
ASHRAE Releases Program for Integrated Design Conference
April 17, 2024
Meet Rick Gopffarth, MCAA's New President
April 16, 2024
Tax Day? Engineering Firms Urge Fixes to Federal Codes
April 16, 2024
Carrier Takes Wall Street, Reports Strong 4Q
Feb. 7, 2024
Fujitsu General America Promotes Hosoi to President
Jan. 18, 2024
Carrier Adds Viessmann Unit in Flurry of Deals
Jan. 5, 2024
American HFC Coalition Applauds Anti-Dumping Probe
Nov. 15, 2023
Members Only Content
HPAC 2023: Our November Quiz!
Nov. 1, 2023
New HVACR Products: October 2023
Oct. 19, 2023
AHR Expo Announces 2024 Innovation Awards Winners
Oct. 14, 2023
Crete United to Partner with ProStar Energy Solution
March 20, 2024
Modular Construction Still Gaining Ground
March 18, 2024
ASHRAE 90.1: Charting the Path to Net Zero Buildings
March 5, 2024
New HVACR Products: February 2024
Feb. 19, 2024
AHR Sessions: Our Collection of Field Reports
Feb. 14, 2024
Members Only Content
HPAC 2024: Our February Quiz!
Feb. 1, 2024
Converting to a Heat Pump? Be Careful!
Feb. 16, 2024
Patterson Appointed Leader of Madison Air’s Heat Group
Jan. 19, 2024
Intellihot Hires Chief Operating Officer
Jan. 18, 2024
ABMA Takes Stock, Looks Ahead with Promise
Jan. 16, 2024
DOE Elevates Four More Heat Pump Manufacturers
Jan. 13, 2024
Ice Air Wins Grant to Make More Electric Heat Pumps
Dec. 15, 2023
AHR 2024: HPAC's Product Highlights, Day 3
Jan. 25, 2024
AHR 2024: HPAC's Product Highlights, Day 2
Jan. 24, 2024
AHR 2024: HPAC's Product Highlights, Day 1
Jan. 23, 2024
EXPO Report: Day 1 Highlights
Jan. 23, 2024
New HVACR Products: January 2024
Jan. 18, 2024
New HVACR Products: December 2023
Dec. 18, 2023