Headline news around the U.S. is filled with stories of commercial business entities as well as government facilities being compromised by hackers, foreign goverments, and malcontents looking to steal data, credit card info, or worse. Unfortunately, these hackers sometimes game access through the building control systems that our readers design and maintain.
In March 2014, sister publication, Contracting Business.com published a column titled, "Cyber Security and the HVACR Contracting Community," that addressed the growing vunerability of commercial buildings to Internet-based attacks. The article focused on an attack on Target retail stores and their customers that apparently happened through an unwitting mechanical contracting firm whose wireless billing systems had also been compromised.
According to a website called FireEye (targets purveyers of threat protection services), "Today's security defenses are failing because, in the battle against cybercrime, security teams are using an outdated arsenal. They rely too heavily on legacy platforms that leverage technology dependent upon signatures—and while these platforms may be good at blocking basic malware that is known and documented, they stand little chance against today's sophisticated, dynamic cyber attacks that occur across multiple vectors and stages."
I daresay that today, many building automation systems (BAS) that are online or that are being designed, don't have the proper level of security against such attacks and leave your clients and building tenants exposed to the wiles of cybercriminals, nation-states, and hacker activists whose attacks are growing increasingly sophisticated and more effective in their efforts to steal and sabotage.
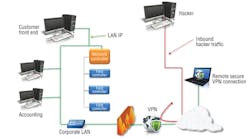
How easy is it to hack into a BAS? My gosh there are articles on the Internet - classes even - that teach HOW to do it and what tools are required to not only successfully penetrate a BAS, but make your access undetectible after you exit. In one instance, a buildings technologies consultant named Phil Zito has posted a step-by-step course on exactly how to do this. To me, it looks as if Zito is using this as a training excersize to teach building systems security personnel what it takes to break into a BAS so they can develop counter-measures, but hackers could also use it for bad deeds.
This is scarey stuff because there are MANY sites that teach the same thing.
In April, during the 2014 Niagara Summit, a bi-annual user-group meeting produced by Tridium, an independent business unit of Honeywell. The summit is attended by developers, programmers, building owners, and engineers who work with the Tridium building automation platform and cybersecurity was the topic of a panel discussion. Panelists represented many companies in the security industry.
Moderator Jeffery Brown, a senior correspondent for the PBS NewsHour show, summed up the discussion with the following takeaways for designers and engineers of building automation systems and facility owners and managers. He said it's vital to:
- Get the cyber security conversation started
- Make security part of the organizational and building DNA
- Seriously budget for security
- Send people to training, and then evaluate their first experience
- Rotate your exisitng or planned system and view it as an “evil bit,” and prepare your worst case scenario answers now — so, if an attack does happen, you control the message and know who is responsible to respond
- Remember that regulations tend to create a culture of minimum compliance
- Also remember that effective cyber security requires good security citizenship — awareness and concern from everyone in the chain at every level.
For the consulting engineering and commercial HVAC contracting industries, the good news is that smart HVAC controls are really the future of the HVAC industry, according to a study, published in March 2014. The study can be found on the Research and Markets website. It says that the smart HVAC controls market is expected to grow at a compound annual growth rate of 8.22% in the next six years (2014-2020). Much of this is due to regulations calling for the industry to up the ante with regard to energy efficiency and smart HVAC controls to accomplish efficiencies either by having sensors that can communicate to the thermostat or with the ability to access an HVAC system over the cloud using a smart-phone application or a web browser.
Businesswise, this is great news, but it also provides cybercriminals more opportunities to cause trouble.
Some statistics bear this out:
In 2005, among more than 7,800 businesses, 67% detected at least one cybercrime against them and of those companies so victimized, 86% detected more than one attack, according to the Bureau of Justice Statistics. They also found that nearly 68% of the victims of cyber theft sustained monetary losses of $10,000 or more. By comparison, 34% of the businesses detecting cyber attacks and 31% of businesses detecting other computer security incidents lost more than $10,000.
The BJS also found that system downtime from cyber attacks or computer security incidents lasted between 1 and 24 hours for half of the businesses and more than 24 hours for a third of them.
Yeah the numbers are old. But you can bet your bottom line that the numbers have more than doubled in the intervening yearsbetween when the BJS study was conducted and today.
The point is, as an industry we have to make building control systems security a key part of our designs. We have to find ways to monitor and test those systems ost ee if they are vulnerable to hacking. ANd we have to keep up with the advancements in technology. Rest assured, the hackers and cyber criminals will.