Cybersecurity: What Every CS Vendor Should Know – Part One
By MICHAEL CHIPLEY, PhD, GICSP, PMP, LEED AP
The PMC Group LLC, Centreville VA
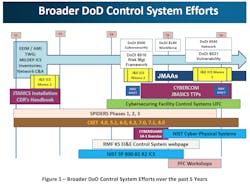
The U.S. Dept. of Defense (DoD) has adopted the Risk Management Framework (RMF) for all Information Technology and Operational Technology networks, components and devices to include Facility-Related Control Systems (FRCS). A major challenge to implement the RMF is to get the architects, engineering, construction, system integrators, and operations and maintenance community trained and capable of performing the RMF tasks and activities. Over the past several years, the Engineering, Installations and Environment (EI&E) directorate has led the broader DoD Control Systems efforts to develop policy and guidance for FRCS as illustrated in Figure 1.
With the recent publication of the Unified Facility Criteria 04-010-06 Cybersecuring Facility-Related Control Systems and the services and agencies submission of their first Cybersecurity Implementation Plans; the FRCS Statement of Work (SOW), Request For Proposal (RFP), and Request For Quotes (RFQ) are now beginning to require the contractor/vendor community to meet the cybersecurity requirements. To meet this need, the DoDEI&E Installations Energy (IE) and the Environmental Security Technology Certification Program (ESTCP) offices have partnered to post RMF policy, guidelines, templates, checklists, resources, and tools on the ESTCP website. The ESTCP website and content is open to any organization, and all ESTCP projects are now required to submit OT RMF packages as part of their submittals.
The web page provides all open source and services/agencies guidance, and the ESTCP guidelines have been developed specifically for ESTCP OT project teams, but can be used by any organization for any project (OT or IT). Contractor/vendors need to become familiar with the terminology and processes as discussed in the following sections. Over the next 2-5 years, two immediate areas of need across DoD are: 1) To create 'Test and Development Environments' (TDE) to perform patching, validation of software and firmware, and penetration testing; and 2) To develop a continuous monitoring capability using both active scanning and passive monitoring techniques.
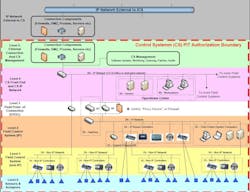
In the past year, the services and agencies have begun or have defined their Platform Enclaves to identify the Authorization Boundary and assign roles and responsibilities to system owners.
PLATFORM ENCLAVE
The designation of the Platform Enclave (PE) and the Authorization Boundary is established by each service/agency. The Air Force PE is shown in Figure 3. Note the change in who will have ownership and O&M responsibilities for the “Traditional IT” Front End of the PE. Prior, when the service/agency received a completed FRCS at turnover, the server, workstation, and laptops became Real Property Installed Equipment that were the Production system and rarely were the systems patched or upgraded to new operating systems, and were not monitored for AV/Malware. In the new process, the FRCS will be bought as a typical MILCON or SRM project, but the CIO will be responsible for owning and maintaining the “IT” portion. The process is still under development, but vendors may be given the alternatives on which IT equipment to provide, or the IT may be provided as Government Furnished Equipment (GFE).
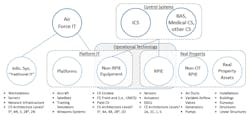
Air Force Platform Enclave
As stated in the new AFGM 2017-32-01, “A CS is considered operational technology (OT), which is IT adapted to directly monitor and/or control physical devices, processes and events where availability is the primary operational concern. Accordingly, OT is more sensitive to the application of cybersecurity measures and controls that can affect its availability. The Authorizing Official (AO) assigned to the CS boundary is responsible for managing the risk for OT and may tailor controls to balance security and availability.
Air Force CE CS consist of OT classified as either Real Property Installed Equipment (RPIE) or Non-RPIE Equipment. Figure 1 represents the elements that comprise CS in addition to OT’s affiliation with the Platform IT (PIT) category of Air Force IT, defined further in AFI 17-101. Referencing AFI 17-101, Platforms and Non-RPIE Equipment would generally be classified as types of “PIT Systems” or “PIT Subsystems.” Figure 4 illustrates the new division of Air Force RPIE and non-RPIE.
NOTE: The division of RPIE and non-RPIE across DoD is still being developed. A further complicating factor is that the CIO and the Electronic Security Systems communities define IT and ESS as Personal Property (PP), which is typically refreshed at the 3-7 year life-cycle, versus the 10-20 year lifecycle refresh for FRCS RPIE OT. In many cases, the IT portion of the OT system cannot be refreshed at the same time as the IT OS and field controller’s OS may be coupled.
The following sections apply to ESTCP projects, but can be used by any organization.
ESTCP CYBERSECURITY GUIDELINE
The ESTCP Cybersecurity Guideline defines the Cybersecurity Procedures for ESTCP OT Facility-Related Control Systems (FRCS) projects. The intention of this document is to provide a general outline and more granular guide for the planning, design, construction, operations and commissioning of the FRCS following the Risk Management Framework (RMF) process outlined in UFC 04-010-06 Cybersecurity of Facility-Related Control Systems. The Energy, Installations & Environment (EI&E) community is responsible for all FRCS related to real property assets (facilities), including but not limited to:
- Control System Platform Enclaves (PE)
- Airfield Systems (AS)
- Pier Systems (PS)
- Environmental Monitoring (EM)
- Electronic Security Systems (ESS)
- Fire & Life Safety (FLS)
- Dam, Lock & Levee Systems (DLL)
- Medical Control Systems (MED)
- Traffic Control Systems (TCS)
- Transportation & Fueling Systems (TFS)
- Meteorological Control Systems (MET)
- Building Control Systems (BCS)
- Utility Control Systems (UCS)
- Utility Monitoring & Control Systems (UMCS)
TEST AND DEVELOPMENT ENVIRONMENTS (TDE)
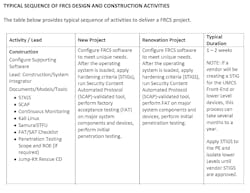
For new or major modernization projects, the Systems Integrator will establish a Test and Development Environment (TDE) that replicates the Production Environment to the highest degree possible starting with the Level 4 Workstations, Servers, software and with at least one of each of the Level 3-0 major components, devices, and actuators. At approximately the 50-75% construction complete, the TDE will be used to perform Factory Acceptance Testing (FAT) of the project to ensure the project has end-to-end functionality, has been properly configured using the Security Content Automation Protocol (SCAP) tool and the Security Technical Implementation Guides (STIGS), all patches (OS and CS) are installed and properly configured, and begin creating the artifacts for the draft System Security Plan. At approximately 95-100% construction complete, the TDE will be used to conduct Site Acceptance Testing of the complete FRCS, and if required, Penetration testing. The SAT artifacts will be included in the final System Security Plan, FMC and Jump-Kit (if required).
FRCS CONTINUOUS MONITORING
The Continuous Monitoring (CM) Strategy has been developed by the DoD using the DISA ESS tool suite for the Level 4 Operations Center servers and workstations. The ESTCP PI and support/system integrator contractors will be given guidance on the tools and applications to use for Level 3 and below components and devices. For ESTCP projects that require connection to the DoDIN, the Project Team will be required to demonstrate the solution is compatible with the FRCS continuous monitoring Host-Based Scanning System (HBSS) and ACASS for Level 4, using active scanning and a FRCS passive network monitoring capability to provide end-to-end monitoring of both legacy systems and new systems that can support end-to-end active scanning. The monitoring capability will be based on a robust, multi-tier architecture that provides local, regional, and NSOC alarm monitoring, as well as remote alarm assessment, dispatch, and response. The multi-tier structure provides multiple levels of FRCS event visibility that corresponds to the DoD Mission Assurance program and includes redundant primary and secondary monitoring capability within regions or in clusters.
For Closed Restricted Network (CRN) projects, FRCS monitoring capability shall be analyzed on a case-by-case basis to determine suitability and cost effectiveness. FRCS contractors cannot use non-approved laptops/ computer and external portable media storage devices on the DoD network; only FRCS/ UCS/ BCS/ DDC government-approved field laptop and portable media will be used for both the Test and Development Environment and the Production system. While no FRCS can be guaranteed to continue to function and operate when a determined advisory has targeted the FRCS, the ability to withstand cyberwar attacks, even if in a degraded state, is a key consideration, particularly for Mission Critical and Mission Essential facilities. Contractors should design, construct, and operate the FRCS in accordance with the USCYBERCOM Industrial Control Systems Advanced Techniques, Tactics, and Procedures 2016. Understanding how to Detect, Mitigate, and Recover from a cyberattack on the FRCS is vital; the Jump-Kit Rescue CD is a key deliverable that defines the Fully-Mission Capable (FMC) Baseline and is the living document that maintains the current FRCS configurations and operating parameters. USCYBERCOM, the Network Security Operations Center (NOSC), and the services Facilities-Related Control Systems Operations Center (FRCSOC) use the FMC to develop and manage the Continuous Monitoring strategy.
Contractor/vendors should align their delivery processes to the guidelines and anticipate future UFC’s to include these types of additional guidance and instruction.
IMPACT OF COST : 'LEED' AS ANALOGY
In the UFC, the statement is made that “while the inclusion of cybersecurity during the design and construction of control systems will increase the cost of both design and construction, it is more cost-effective to implement these security controls starting at design than to implement them on a designed and installed system. Historically, control systems have not included these cybersecurity requirements, so the addition of these cybersecurity requirements will increase both cost and security. The increase in cost will be lower than the increase in cost of applying these requirements after design.”
While the cybersecurity requirements can appear to be daunting and adding additional cost, the cost to not meet the cybersecurity requirements could result in loss and damages far in excess of the new requirements. A key objective is to make cyber a part of the normal business practice within the next 5 to 10 years. As an analogy, if we look at how LEED evolved, the federal government made LEED Bronze a requirement and budgeted for the additional costs. At the early stages, there were few A/E’s with design certifications, few green products, and green construction techniques were being developed. By 2005, an owner could get a LEED Silver building for the price of a LEED Bronze, and today a LEED Gold or Platinum building comes at virtually no cost as the market price has now become the norm.
SUMMARY
OT cybersecurity is a new area of practice for most contractors and vendors supporting the DoD. Organizations that do not train their staff and prepare their FRCS to meet the new requirements will not be competitive in the market. The ESTCP website is meant to be a “One Stop Shop” for any organization to begin the journey to becoming cybersecurity subject matter experts and deliver cybersecure FRCS to the DoD.
___________________________________________________________________________
In January 2018, the second article in this series will focus on the Control System Vendor corporate business IT systems that store and transmit Controlled Unclassified Information (CUI), which typically includes the CAD, BIM, technical specifications and operating manuals about the OT system. A hard copy of this article will appear in the December 2017 print edition of HPAC Engineering magazine.